티스토리 뷰
Hunting on ASPX Application For P1's [Unauthenticated SOAP,RCE, Info Disclosure]
elmahdi 2020. 5. 31. 18:52Hi, I wanna share with you how i found a P1 Vulnerabilities in a private program.
At first i grabbed subdomains and titles via assetfinder and, then resolved them using httprobe and extracted the the title of the responsive ones with get-title.
I started looking at the titles and i saw that there is a title that had "LOGIN" in it, i opened that page in my browser and i found that the website is an ASPX Application, the page didn't have any link for me to register, so i tried directories discovery with ffuf in orded find pages and sensitive files but i didn't find anything interesting so i moved to the next strep wich is Google search engine, i just made a basic dork search :
site: care.redacted.com
I opened all the pages and i noticed that there's a page for registeration but i didn't have the informations needed to do register myself :( , I clicked on CTRL+U to see if there are any JS Files that are included in the page and i found these two Files
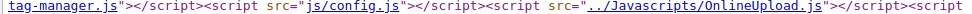
Unauthenticated SOAP To [ Delete Documents, Get Informations Of Users, Access To Messages Of User , And Information Of Any Configuration of System, Other Functions ] :
I opened the config.js file and i found a SOAP File.
/services/CareRedactedredacted.asmx/ 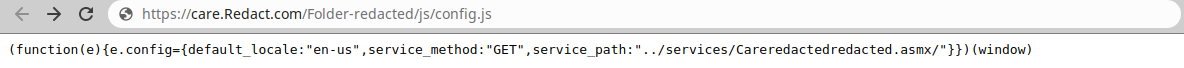
I opened the SOAP file and i found many user and system functions, i thought these function will surely require credentials, i coppied one of the urls that had a parameter id wich i gave it a radom value : 328915 and made the request.
https://care.redacted.com/services/CareRedactedredacted.asmx/GetCustomerinfobydoc?Redacted=string&id=328915Surprise, the website returned all the user sensitive informations without any authentication !!
Remote Command Execution in Telerik UI via CVE 2017-9248 And Critical IDOR thats Leak all Users PII :
After i reported the SOAP bug, i opened the second JS File , i found that theres an URL For an ASPX page wich had an upload functionality( Ohh !!) I tried to upload malicious files such as [ aspx , asp , html ] but it didnt work, and even uploading a valid file ( PDF ) the website would not return the URL for the document or the id for it ( Oh shit ) but i noticed thats the website uses Telerik for uploading the files and managing them ( Amm ) I searched for Telerik Exploits in Google and i found a blog that showed how to Pwn Telerik.
https://captmeelo.com/pentest/2018/08/03/pwning-with-telerik.htmli read it and understood and tried exploiting it, and It worked, I got access to Telerik Filemanager and uploaded a TXT file to confirm the vulnerability.
After reporting the RCE, I returned to the page and i clicked cheked the source code of the page, and i found that there is an aspx File inside the JS Code (Oh) that was for reading Documents !!
var url = '/DocumentManagement/' + 'ViewDocumentImage.aspx?id=' + docid;I Copied the URL And gave the id parameter a random number 15, the website returned PDF document wich had sensitive informations about a user without any authentication !!
Tomnomnom Tools :
github.com/tomnomnom/hacks/tree/master/assetfinder
github.com/tomnomnom/hacks/tree/master/get-title
tomnomnom/hacks
A collection of hacks and one-off scripts. Contribute to tomnomnom/hacks development by creating an account on GitHub.
github.com
Special Thanks to Anass Sbai @Flashy911 for rewrite this post And thanks to 之𝛜𝓭 ン挨ぁ @zedsec009 ♥️♥️
